
Social engineering in cyber security takes advantage of human behaviours and natural tendencies. Social engineering attacks are conducted by analysing how users react if a fake offer or scenario is presented. It exploits human psychology to manipulate people into making security mistakes and giving away confidential information.
Phishing
Phishing is the most common social engineering attack in cyber security. Victims are tricked into providing confidential information by creating a sense of urgency, curiosity and fear. Phishing is usually conducted through emails or text messages. However, it can also be done via catchy pop-ups.
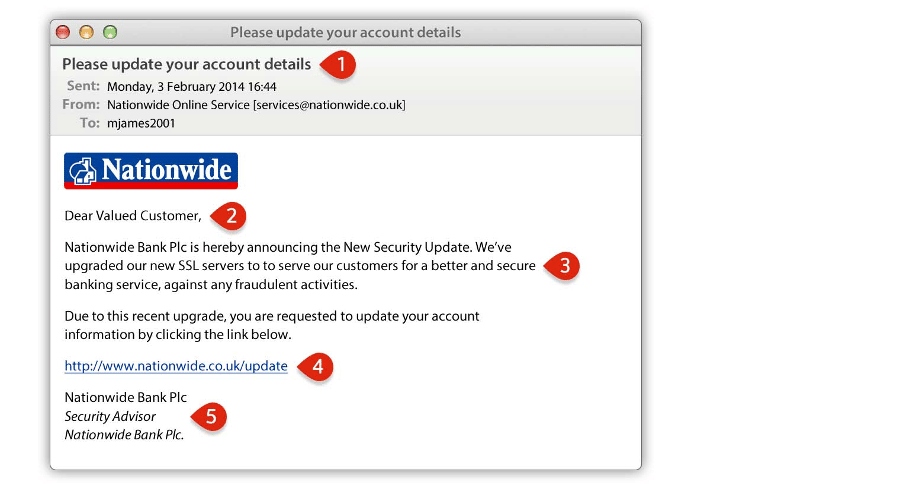
Taking an example of a phishing email scam from Nationwide, a fake email claiming to be from an official bank organisation can be sent to thousands of users asking them to update their account information urgently for security purposes. Usually, the mail would contain a link that would redirect the user to a fake website identical to the bank's original website. Finally, users would enter their banking details and fall into the hacker's trap.
Spear Phishing
Spear Phishing is a more specific version of phishing. It is a personalised attack on one particular victim who possesses critical information. Hackers intend to steal information about the victims by getting their login details or installing malware. Victims are typically those in charge of the company's confidential information.
Baiting
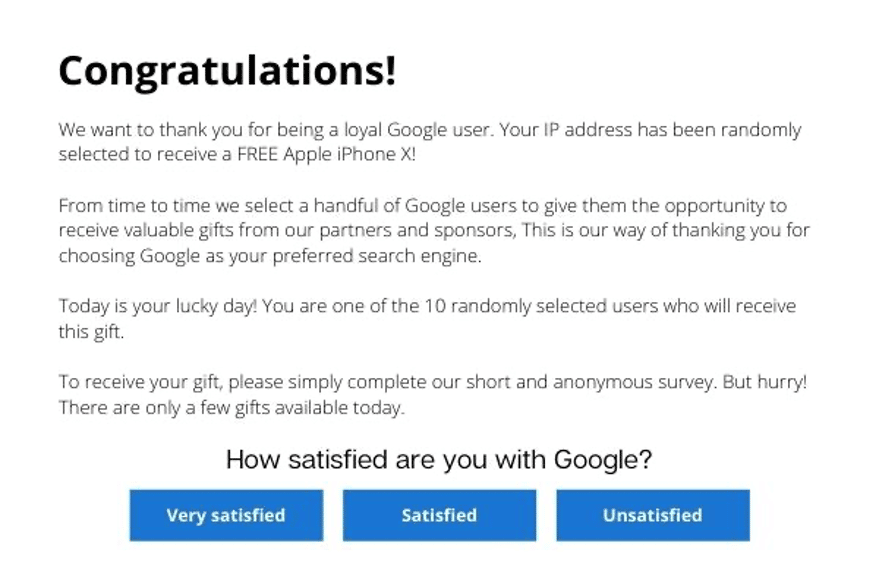
Baiting is like phishing attacks. Baiting is the promise of items or goods that hackers use to entice victims. Baiting relies heavily on psychological manipulation to induce particular actions that are potentially harmful. Baiting also persuades a victim into a trap by promising attractive rewards. The main goal is to steal confidential information or access an organisation's internal network. Baiting attacks are not only restricted to online schemes. Attackers also exploit human curiosity in physical media. For example, pictures may offer users free music or movie downloads to ensure they can easily log in to any website by getting the user's data.
Scareware
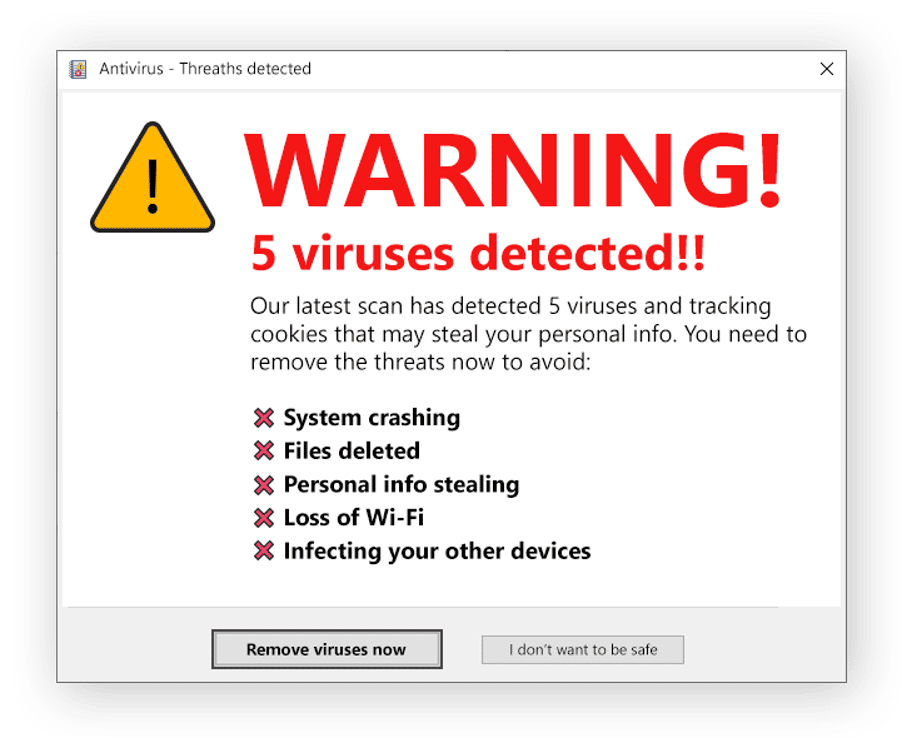
Scareware refers to scam tactics and fake software applications that cybercriminals use to create feelings of panic and fear. Hackers do this to get users to make irrational split-second decisions and trick them into buying worthless software, downloading malicious software or visiting websites that auto-download. Scareware scammers use social engineering tactics in language that creates a sense of urgency in their targets to compel their targets to act. In addition, hackers frequently rely on pop-ups that look like anti-virus alerts.
Increase Awareness
The first step to avoiding social engineering attacks is awareness of such attacks. Companies must host training sessions for all employees and educate them against these scams. Also, companies should have rules to avoid critical information thieving, like never entering login information by clicking the link in the email. Instead, users should enter information by manually entering the URL in the browser.
Protecting your privacy
Increase Security Level
Hackers use malware to affect the computer systems of the victims. For example, they might use spyware and keylogging to collect crucial data. Your company should install robot security to block such malware. The traditional anti-virus isn't capable of detecting advanced threats, so they need to get an anti-malware subscription for employees.